About this update The Windows Root Certificate Program enables trusted root certificates to be distributed automatically in Windows. Usually, a client computer polls root certificate updates one time a week. After you apply this update, the client computer can receive urgent root certificate updates. We found that the root CAs were out of date on some of our Windows 2012 R2 servers. Having investigated this is appears Microsoft released a patch to provide the ability for 'Controlling the Update Root Certificates Feature to Prevent the Flow of Information to and from the Internet'.This patch introduces new registry keys for stopping Windows Update from updating the root CAs along with.
- How To Update Root Certificates
- Windows 10 Root Certificate Update Download
- Windows 10 Root Certificate Update Offline
- Windows 10 Automatic Root Certificate Update
!! Important Warning before proceeding !!
The instructions below describe how to manually update the root certificate store from Microsoft using tools documented by Microsoft. Importing other certificates than the one's provided via Windows Update can pose a serious security risk to your Windows installation. Always take extra care when working with certificates. Corporate computers that are domain joined may also apply policies that may restrict the following procedures. Please consult with your IT department.
In order for FDI Package signatures to be validate, the workstation that is running the reference run time environment (RRTE) needs the proper root certificates installed. Without these roots install, the RRTE could return a failure when validating the signatures and certificates. Even though a failure is reported, the RRTE will still permit you to import the package for testing.
There are several Certification Authorities (CAs) that participate in Microsoft's Trusted Root Certificate Program. For example, companies like Digicert, GlobalSign and Comodo are just a few that participate as of this article. Most Package developers obtain code signing certificates from CAs like these. You can read more about it here: https://technet.microsoft.com/en-us/library/cc751157.aspx
Issue
Not all root certificates are installed by default. For many applications, Windows installs these on demand using Windows Update. However, Microsoft does not publish an API for this 'just in time' installation, and the current RRTE will not trigger Microsoft to download a potential missing certificate. Without this certificate, a signature cannot be validated. This may result in a false failure.
Note: There are typically one or more Intermediate Certificates between the root certificate and the certificate used to sign the FDI Package. The FDI Package sign tool allows the package producer to supply all intermediate certificates necessary build the trust relationship. Therefore, there is no need to pre-install intermediate certificates since they are supplied with the FDI package. While technically the FDI Package could also include the root certificate, this would not help because ultimately, this root certificate must explicitly trusted by the verifying application. See https://en.wikipedia.org/wiki/Root_certificate
Workaround
There is a manual way to install the current root certificates using tools already provided by Windows.
First, you need to download the complete root certificate list using the certutil command line tool (Windows 10 requires administrator rights while using cmd.exe).
You can find a reference to this at:
After running certutil above, this will generate a file called roots.sst This is a container for all current trusted root certificates.

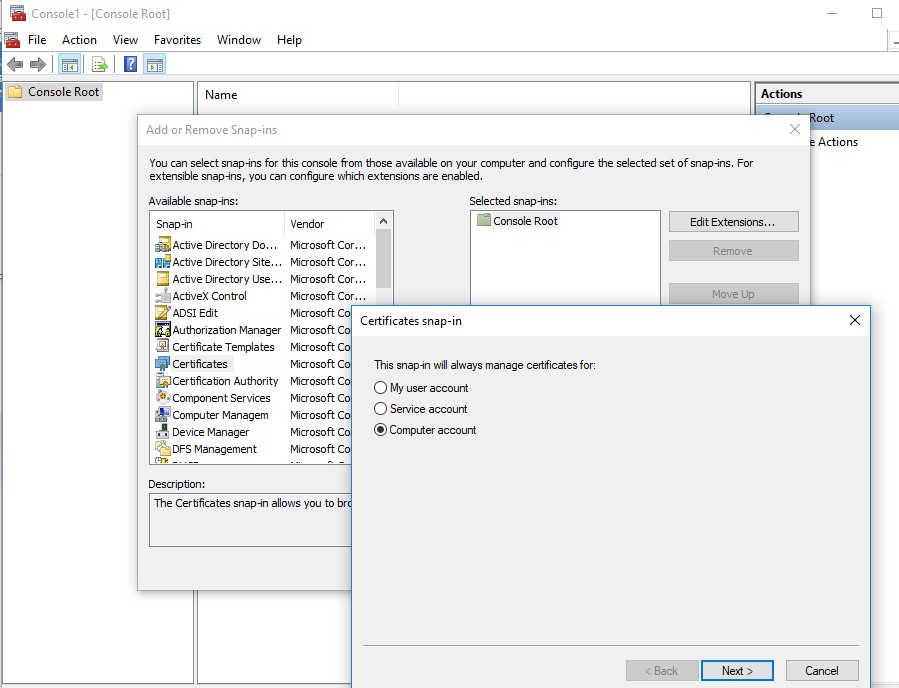
Next, you will need to install these by launching Microsoft Management Console with the Certificate Snap-in. From a command link, enter:
This will open a window that should look like this:
From there, Select Certificates under 'Trusted Root Certification Authority', right click and select 'Import' as shown below.
This will start the Wizard. Click Next to begin
Use the browse button to find root.sst you generated above in the C:Windowssystem32 folder. You will need to change the file type to Microsoft Serialized Certificate Store or the file will not show up.

With the file select, click Next
Now, this part is important otherwise you may get unexpected errors. Make sure to change the radio dialog to 'Automatically select ...' as shown below. Then click Next.
The reason? We have seen at least one instance where an intermediate is also provided in the root.sst file. This will show a warning if you request all certificates into the Trusted Root Store. By selecting Automatic, the certificates will be properly imported.
How To Update Root Certificates
The next screen will show the final step. Click Finish.
Windows 10 Root Certificate Update Download
You should get a confirmation message.
Windows 10 Root Certificate Update Offline
Windows 10 Automatic Root Certificate Update
You can close all windows. The root certificate store is now up to date.
You may see Security Warning messages for each new certificate being imported. If you are unsure if they should be installed, consult with your IT department.